What does talking to AI mean? Is it like talking to an Alexa? Well yes, but not in the way you’re accustomed to. With the release of popular large language models (LLMs) and interfaces for users to interact with them (e.g. ChatGPT), the user act of talking to AI has taking on an entirely new meaning that will change every human’s life for forever. If you don’t have experience yet using the now infamous ChatGPT from OpenAI, I highly suggest you try it out. Ask it anything and discover what it can or can’t do for you.
To get the highest quality output of any AI or an Internet of Things (IoT) machine/device, or any software interface such as a chatbot, we humans must learn how to effectively communicate with the AI that controls it. This communication consists of an input query or command given to the AI, called the Prompt. The output the AI gives you in response is called the Completion. So the act of communicating with an AI can be referred to as ‘Prompting’.
How do you Prompt? Basically, you ask questions or provide instructions using natural language to an AI interface the way you would to a magic genie. What you say or request of it is entirely up to you and your use cases. What output you get in return is conditional on a number of factors, but for simplicity’s sake, two things are super important:
1) the quality of your Prompt (how well do you communicate what you want?);
2) the AI’s knowledge depth for the subject matter in the prompt (does the AI ‘know’ the subject matter of your prompt, and how well does it know it -eg SME level? Junior level? etc.)
As humans, learning how to effectively prompt is essential to leveraging AI to its greatest potential to help us in work and play.
Example: Make me a Study Guide…
Here is an example Prompt good for the Education domain (educators/teachers/students, Instructional System Designers). We uploaded a Cybersecurity Threat Intelligence training YouTube video into OMP! for processing. By doing so we gave our AI the specific subject matter knowledge it needs to answer intelligently a user’s natural language request/question/query (the Prompt) against that particular training material.
Prompt: Make a study guide for this module that includes that following: – high-level summary of the module – overview of each topic covered in the module – for each topic, provide a summary of the key concepts and key key terms under each key concept – a list of recommended external web resources (along with its URL) for further study for each key concept. – The study guide should be in an outline format.
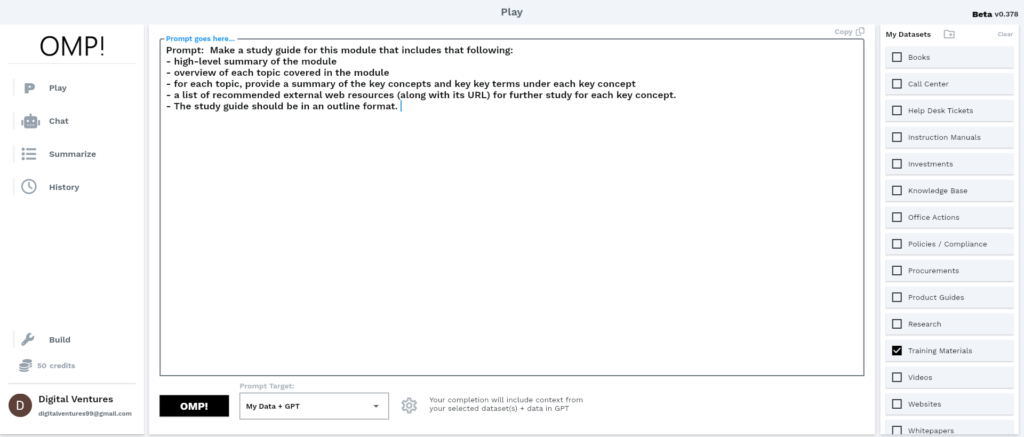
As you can see we tried to give the AI specific guidance such that the output has the content depth and format we desired. And we also didn’t use perfect grammar (used ”that following” instead of ”the following”), which LLM’s don’t need for processing.
After clicking the OMP! button and using the default logic chain, here was the response from OMP! in about 15 seconds time (which utilizes OpenAI’s GPT and other LLMs to process requests about data you feed it):
Completion: Module 2: Mapping Cyber Threat Intelligence to ATT&CK
High-Level Summary:
This module covers the process of mapping cyber threat intelligence (CTI) to the ATT&CK framework. It explains the importance of understanding attack before mapping to it, and provides an overview of the mapping process. It also covers the importance of researching behaviors and comparing results to other analysts.
Overview of Topics:
- Understanding Attack
- Mapping from Finished Reporting
- Mapping from Raw Information
- Storing and Analyzing Data
- Exercise 2
Topic 1: Understanding Attack
Key Concepts:
– Attack: A coordinated set of activities that an adversary uses to achieve a specific goal.
– Tactics: The specific actions an adversary takes to achieve their goal.
– Techniques: The specific methods an adversary uses to carry out their tactics.
Key Terms:
– Adversary: An individual or group that is attempting to gain unauthorized access to a system or network.
– Attack Lifecycle: The stages of an attack, from initial reconnaissance to post-exploitation.
– Tactics: The specific actions an adversary takes to achieve their goal.
– Techniques: The specific methods an adversary uses to carry out their tactics.
Recommended External Resources:
– ATT&CK Overview: https://attack.mitre.org/
– Attack Presentation: https://www.sparkcon.com/talks/attack-presentation/
Topic 2: Mapping from Finished Reporting
Key Concepts:
– Mapping Process: The process of mapping CTI to the ATT&CK framework.
– Step 0: Understanding attack.
– Step 1: Identifying behaviors.
– Step 2: Researching behaviors.
– Step 3: Identifying tactics and techniques.
– Step 4: Comparing results to other analysts.
Key Terms:
– CTI: Cyber threat intelligence.
– ATT&CK: Adversarial Tactics, Techniques, and Common Knowledge.
– Behaviors: The actions an adversary takes to achieve their goal.
– Tactics: The specific actions an adversary takes to achieve their goal.
– Techniques: The specific methods an adversary uses to carry out their tactics.
Recommended External Resources:
– ATT&CK Overview: https://attack.mitre.org/
– Exercise 2: https://attack.mitre.org/training/cti/exercise2/
Topic 3: Mapping from Raw Information
Key Concepts:
– Mapping Process: The process of mapping CTI to the ATT&CK framework.
– Step 0: Understanding attack.
– Step 1: Identifying behaviors.
– Step 2: Researching behaviors.
– Step 3: Identifying tactics and techniques.
– Step 4: Comparing results to other analysts.
Key Terms:
– CTI: Cyber threat intelligence.
– ATT&CK: Adversarial Tactics, Techniques, and Common Knowledge.
– Behaviors: The actions an adversary takes to achieve their goal.
– Tactics: The specific actions an adversary takes to achieve their goal.
– Techniques: The specific methods an adversary uses to carry out their tactics.
Recommended External Resources:
– ATT&CK Overview: https://attack.mitre.org/
– Exercise 2: https://attack.mitre.org/training/cti/exercise2/
Topic 4: Storing and Analyzing Data
Key Concepts:
– Data Storage: The process of storing CTI data in a secure and organized manner.
– Data Analysis: The process of analyzing CTI data to identify patterns and trends.
Key Terms:
– CTI: Cyber threat intelligence.
– Data Storage: The process of storing CTI data in a secure and organized manner.
– Data Analysis: The process of analyzing CTI data to identify patterns and trends.
Recommended External Resources:
– ATT&CK Overview: https://attack.mitre.org/
– Google with Kapidia: https://www.google.com/search?q=kapidia
Topic 5: Exercise 2
Key Concepts:
– Exercise 2: An exercise to map a cyber threat intelligence report to identify the different attack techniques in it as well as the tactics.
Key Terms:
– CTI: Cyber threat intelligence.
– Exercise 2: An exercise to map a cyber threat
Completion #1 Analysis:
So the response was good but very verbose. Maybe a bit difficult to use by a student. We can try to be not quite as specific in our prompt, and see how the completion varies.
Let’s try again with a slightly varied, less specific Prompt:
Prompt: Make a study guide for this module that provides an overview of the topics covered in the module, a summary of the key concepts, a list of the key terms, and a list of the recommended external web resources (along with its URL) for further study. The study guide should be in an outline format.
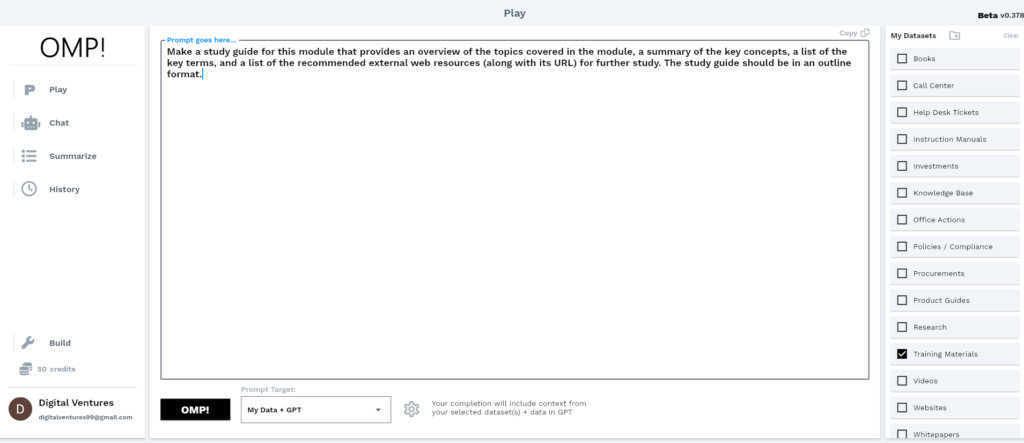
After clicking the OMP! button and using the default logic chain, here was the response from OMP! in about 10 seconds time (which utilizes OpenAI’s GPT and other LLMs to process requests about data you feed it):
Completion:
Module 2: Mapping CTI to Attack
Overview:
This module covers the process of mapping cyber threat intelligence (CTI) to attack. It explains the steps involved in the process, such as understanding attack, mapping from finished reporting, mapping from raw information, storing and analyzing the data, and making defensive recommendations.
Key Concepts:
– Attack: A coordinated set of activities that are designed to achieve a malicious goal.
– Tactics: The high-level strategies used by attackers to achieve their goals.
– Techniques: The specific methods used by attackers to carry out their tactics.
– Mapping CTI to Attack: The process of identifying the tactics and techniques used by attackers based on the CTI available.
Key Terms:
– Attack: A coordinated set of activities that are designed to achieve a malicious goal.
– Tactics: The high-level strategies used by attackers to achieve their goals.
– Techniques: The specific methods used by attackers to carry out their tactics.
– Mapping CTI to Attack: The process of identifying the tactics and techniques used by attackers based on the CTI available.
– Finished Reporting: Reports that have already been analyzed and summarized.
– Raw Information: Unprocessed data that has not been analyzed or summarized.
Recommended External Web Resources:
– Attack Presentation by SparkCon: https://www.sparkcon.com/presentations/attack-presentation/
– Google with Kapidia: https://www.google.com/search?q=kapidia
– TAQDA Miter: https://attack.mitter.org/
Completion #2 Analysis:
So not quite as detailed a completion as seen from the former more granular prompt, but still pretty good. This completion is more synthesized, and could be easier for a student to digest and actually use.
An educator can play with prompting by ‘tuning’ the prompt until the desired content outcome is achieved.
